Spacemesh has been fighting to raise awareness about Digital Privacy, because we believe that privacy is human right that needs to be protected. This is why we’re so passionate about helping to build Web3!
Recently, in the “Pro Tips” drop challenge, we asked our community to send in helpful tips and tricks for protecting digital privacy in the age of surveillance capitalism. They more than delivered.
Here, we’ve compiled all tips that met the challenge criteria. Due to some having the same advice, we included them on a “first come first serve” basis.
(Disclaimer: these are community-submitted tips. We have posted them here on the assumption that they’ve all been submitted in good faith, but we advise that you use discretion if you decide to follow any of the instructions below.)
Table of Contents:
-- Access Instagram secretly
-- Keep metamask wallet safe
-- Revoke smart contract approvals on platforms like Ethereum
-- Don’t scam seed phrase & general digital hygiene rules
-- Save multiple wallet seed phrases
-- Limit data collection by Facebook’s partners
-- Protect against spam messages on Discord
-- Protect yourself when buying tokens on DEX
-- Protect the passwords you use incorrectly from hackers
-- Disable auto join group on Telegram
-- Telegram privacy settings
-- Use private browsing in the Safari web browser on Mac
-- Security and protection features for Whatsapp
-- Use Whatsapp secret chat
-- Open secure boot utility on Mac
-- Hide activity status on Facebook for Android
-- Personal data security across various platforms, such as DEX
-- Export mnemonic seed phrase on Keplr wallet
-- Preventing email tracking on Gmail
-- Two-factor authentication for Gmail
-- Make secure transactions on CEX exchanges
-- Make secure withdrawals on CEX exchanges
-- Enable open access to the internet by running VPN node servers
-- Phantom wallet security
-- Secure accounts on CEX exchanges
-- Security tips when using VPNs
The Tips and Tricks
DaniF
Platform: Instagram app
Purpose: Being able to access Instagram without anyone knowing, especially on work time.
Instructions:
1. Open up the Instagram app on your phone. 2. Navigate to your profile by tapping your profile picture on the far right of the bottom navigation bar. 3. Click the menu icon on the top right-hand corner. 4. Tap the menu item that says Setting. 5. Click Privacy to enter your privacy settings. 6. Click Activity Status under the Interactions heading. 7. Once you reach the Show Activity Status option, toggle it off.
Chainguys
Platform: metamask extension on chrome
Purpose: to check and clean “weird” authorization to keep wallet safe
Instructions:
1. Open up chrome and navigate to top right-hand corner and you see metamask’s lovely fox logo. 2. Click logo, wait for pop-up, log in and choose one account you wish to operate 3. Again find top right-hand corner, you see a “3 dots” symbol which stands for “account option”,click it and new pup-up emerges. 4. Click “connected sites”, there you go, just check if each is the one you wish to connect and click “disconnected” for each one you feel sick or unsafe.
andreiv
Platform: Any EVM compatible chain, for example Ethereum
Purpose: Revoke smart contracts approvals.
Background: For any transaction on the Ethereum chain, before executing the transaction itself, the smart contract needs approval to transfer your ERC20 or ERC721 tokens. Most dapps ask for approval for a really high number, just to make sure it covers all users cases and “improves” the user experience. This is a bad security practice and you should revoke all approvals after you’re done interacting with a smart contract (for example you are no longer interested in a yield farm).
Instructions:
1. Go to your chain explorer - Ethereum: https://etherscan.io/tokenapprovalchecker
- Polygon: https://polygonscan.com/tokenapprovalchecker
- Avalanche: https://snowtrace.io/tokenapprovalchecker
- You can probably find it for other chains as well
2. Log in with your web3 wallet. 3. Go to “Approval” tab. 4. Under “Assets” you can see the asset which can be spent. Under “Approved Spender” you can see which smart contract can spend your assets. 5. Disable anything you are not using.
Obzen
Platform: All Crypto Wallets with a seed phrase
Purpose: Don’t scam seed phrase
Instructions:
1. Create new wallet 2. DON’T copy seed phrase in cash on your device 3. DON’T photo seed phrase 4. Only “hardware copy”:
- Take a pen and write down the phrase in a notebook
- Better in 2-3
- Or use special Cold Storage Seed Backup. For example Spacemesh Cold Storage Seed Backup ;)
- Put the notebooks/Storage away in places only known to you. For example, safes, bank cells, a box with documents
- Do not tell anyone the phrase, the place of writing and storing the notebook. It is possible to inform your lawyer to include the wallet in the will
Platform: Our Brave New World
Purpose: Digital Hygiene Rules
Instructions:
- Do not use birth dates, pet names, or even the names of mom’s girlfriends in passwords
- Do not leave your personal phone number, date of birth, family ties, credit card number in open access on social networks. And anyway, you shouldn’t tell everyone everything about yourself
- Don’t store all passwords in one password app! These are targets for hacker attacks. Store important passwords, including seed phrase, on paper or special metal Storage
- Check your financial transaction history regularly
- Update your antivirus regularly
- Check the sites on the scam before connecting your crypto wallet
- Don’t be stupid! Think before you do something
hungph
Platform: Metamask, phantom
Purpose: save multiple wallet seed phrases (100 wallets and more)
Instructions:
+ Create text file to save all seed phrase of each walet into that (matamask for 1 file, phantom for 1 file) + change tail of filename from .txt to img or any other type of file that cannot read + Compress file and setup password + save all files to 2 USB and delete file from local computer
CryptoCat
Platform: Facebook
Purpose: Limit Data Collection by Facebook’s partners
Instructions:
On a computer:
Click the down arrow in the top right of the Facebook home page > Settings & Privacy > Settings > Apps and Websites > See More > Click on the box next to the app’s name > Remove!!!
EvgeniyLEV
Platform: Discord
Purpose: to disable the distribution of messages from server members to provide protection against spam and accidental navigation to dangerous sites.
Instructions:
- select one of the available servers in Discord
- on the computer in the upper left corner near the server name, click on the drop-down menu, select privacy settings; on the smartphone, press the three dots next to the name of the server.
- in the window that opens, disable private messages from server members.
ruslan klinkov
Platform: Any DEX
Purpose: How to protect yourself when buying a token on dex
Instructions: Very often fake copies of tokens are traded on DEX. To avoid becoming a victim of scammers, check the token smart contract:
- Go to Coinmarketcap or CoinGecko
- Copy the token smart contract (pic1)
- Go to any DEX (for ex Pancakeswap)
- Select “Trade” in the token exchange window insert the address of the smart contract. The real token icon will appear (pic2)
- Tap “Add” And you’ll see the original token on your Metamask
Now you can trade.
Be attentive and trade with caution on DEX
Vitaly
Platform: Any web browser
Purpose: Security. To avoid revealing your wrong password to hackers
Instructions:
- All we know that we have to use different passwords on different sites. However it is hard to remember all passwords
- Sometimes we make mistake and enter wrong password that is belong to other site
- Current site shows “wrong password” message, however your input has already been registered and your password from other site has been cached
- Hackers would be able to collect passwords you have entered incorrectly on insecure site, track your browsing history and hack your account on other site
- Tip: be careful when enter login and password. Try to use the one that fits current site only. Change passwords frequently, especially important ones
cascoigne
Platform: Telegram
Purpose: disabled auto join group
Instructions:
1. Open the Telegram app 2. Select Settings 3. Select Privacy and Security 4. Tap group, and change ‘Who Can Add Me’ from ‘Everybody’ to ‘My Contact’
Tokenomist
Platform: Telegram
Purpose: Telegram Privacy Settings
If you don’t want to share personal information with Telegram users, I recommend setting the privacy of your profile. To do this, go into the privacy settings and change the values you set - by default, all of this data and features are available to everyone.
Instructions:
— Phone number - Who can see my phone number - Nobody
— Phone number - Who can see my phone number - My contacts
— Recent activity - Who can see when I’m online - Nobody
— Profile picture - Who can see my picture - My contacts
— Calls - Who can call me - My contacts (or Nobody, if this feature doesn’t interest you at all)
— Calls - Peer-to-peer - My contacts (or Nobody if you prefer not to share your IP-address)
— Forwarding messages - Who can refer to my account when forwarding messages - My contacts
— Groups and channels - Who can invite me - My contacts
AnnaLapteva1010
Platform: Browsing in Safari on Mac
Purpose: Use Private Browsing in Safari on Mac
Instructions:
With Private Browsing Mode, Safari doesn’t save your browsing history and the websites you visit aren’t shared with your other devices. - In the Safari app on your Mac, choose Safari -Preferences, then click General. Click the “Safari opens with” pop-up menu, then choose “A new private window.” If you don’t see this option, choose Apple menu - System Preferences, click General , then make sure “Close windows when quitting an app” is selected.
Victorius
Platform: WhatsApp controls
Purpose: Security and Protection Features that you can customize to your liking to stay safe.
Instructions:
Use your privacy settings to control who can view your information. You can set options separately for last seen time, profile picture, details, or status.
- All. Last seen time, profile photo, details or status will be visible to all WhatsApp users.
- My contacts. Last seen time, profile photo, details, or status will only be visible to contacts in your address book.
- My Contacts Except…. Last seen time, profile photo, details, or status will be visible to contacts in your address book, except those you have excluded.
- Nobody. Your last visit time, profile photo, details, or status won’t be visible to anyone.
WhatsApp will automatically set your privacy settings as follows:
- Any WhatsApp user can see your read receipts, the time you last visited, your details, and your profile photo.
- Your contacts can see your status updates.
To change these settings, just go to WhatsApp > Settings > Account > Privacy.
Note:
- If you hide your last seen time, you won’t be able to see other users’ last seen times.
- You cannot hide your status online or typing.
- If you disable Read Receipts, you will not be able to see other users’ read receipts. Read receipts are always visible in group chats.
- If a contact has turned off read receipts, you won’t be able to see that they’ve viewed your status update.
Anna Vrabi
Platform: Telegram
Purpose: confidentiality of your correspondence
Instructions:
1. Open the profile of the user you want to contact. 2. Tap on ‘…’, then ‘Start Secret Chat’.
- Remember that Telegram secret chats are device-specific. If you start a secret chat with a friend on one of your devices, this chat will only be available on that device. If you log out, you will lose all your secret chats. You can create as many different secret chats with the same contact as you like.
Gleb2392k
Platform: Mac computers
Purpose: Open the secure boot utility
1. Turn on your Mac, then press and hold the Command (⌘)-R keys when the Apple logo appears. Your Mac will start in macOS recovery mode. 2. When prompted to select a user whose password you know, select that user, click Next, and enter the administrator password. 3. When the macOS Utilities window appears, choose Utilities > Secure Boot Utility from the menu. 4. When prompted to authenticate, click Enter Password for macOS, select an administrator account, and enter the password for it.
MrPiero
Platform: Facebook Android
Purpose: Hide activity status
Instructions:
If you want to be sure that your active status on Facebook won’t be seen, switch your status to more “off” on all devices where you use Facebook.
1. Open the Facebook app. 2. Click the menu icon in the top right corner. 3. Scroll down to the “Settings and Privacy” section. Click Settings. 4. Scroll down to the Privacy section and click Online Status. Move the switch to the off position and confirm. 5. Now friends can’t identify you as online.
Alisa
Platform: DEX, browser, wallets
Purpose: personal data security
Instructions (advices) :
- ️Do not connect to public Wi-Fi networks
- ️If necessary, give internet from your phone to computer and connect to your own Wi-Fi
- ️If the computer prompts you to save the password - Click on the “do not save password” button
- ️Create new passwords for each site, do not use the same passwords
- ️Never copy seed phrases and passwords to the clipboard. Write exclusively on a piece of paper
- ️Always check the spelling of the site so as not to fall for fake
- Update metadata regularly
- For crypto work, use a separate mail. Do not list it anywhere except crypto
Do not download dubious applications or extensions to your phone/computer
Andrrrey
Platform: Keplr wallet.
Purpose: Export of Mnemonic Seed Phrase.
Instructions:
- In the extension click on the silhouette in the upper-right corner.
- Click on the three dots and in the drop-down menu select [View Mnemonic Seed].
- Confirm the operation by writing your Password.
- Copy the Mnemonic Seed Phrase and store it in a safe place.
Remember that taking a screenshot as well as storing the words in an unsecured, internet-connected device is extremely dangerous.
tenko
Platform: Gmail(iPhone)
Purpose: Preventing email tracking
Instructions:
1.Open the gmail iphone app 2.In the top left, tap Menu 3.Tap settings your account 4.Tap images 5.Ask before displaying external images
There is a technique in email called tracking pixels that collects information about email openings and recipients by using a single pixel of a transparent image to detect its reading.
If information such as the recipient’s IP address is leaked by tracking pixels, it could be misused in crimes such as phishing scams.face_with_monocle
Slatonega
Platform: Gmail.
Purpose: To prove that you are the owner of this account.
Instructions:
1. Log in to your Gmail account 2. Go to the Two-step Authentication page 3. Select Proceed 4. Follow all the setup steps 5. When you are done, you will be taken to the Two-step Authentication settings page 6. Check all settings and add account verification methods. 7. Save backup login codes when there is no internet connection.
mr vakulin
Platform: CEX Exchanges
Purpose: to provide financial resources. Making secure transactions
Instructions (tips):
- When registering on a centralized exchange, you must use a separate crypto mail
- Pass KYC to get full access to the functionality
- If the computer prompts you to save your password - Click on the “do not save password” button
- In the security settings, you must enter your mail, phone number and Google Authenticator
- When choosing a seller, you need to pay attention to the number of transactions, the more, the better.
- When transferring funds during the transaction, carefully check the details provided by the seller and read the comments
Make deals with trusted stores. Always make payments on your own behalf and indicate the purpose of payment stated by the seller to avoid problems with deposits
Аlenka Ali
Platform: CEX Exchanges
Purpose: Security of funds withdrawal from the exchange to the wallet.
Recommendations:
- Choose a coin.
- Enter the withdrawal address.
- Choose a Network (be sure to pay attention, otherwise your funds will not be returned).
- Next, we send a PIN code to the phone and email, enter and do not forget to enter Google Authenticator.
Be careful when withdrawing funds from the exchange to wallets.
Paktra
Platform: Mystnodes.com
Purpose: To enable open access to the internet by running VPN node servers. It’s one way to make the web blind to borders.
Instructions:
1. Go to mystnodes.com and create an account using your anonymous email address.
2. In the HOME tab, click on GET STARTED.
3. Select the Device that you are using to run the VPN myst nodes. (For this instruction, we will use raspberry pi 3.)
4. After selecting Raspberry Pi, the hyperlink will take you to select “Installation type”
5. Click on, “I have RPI device”
6. The next step will be to follow the instruction provided which I will elaborate on some more below.
7. So we are going to set up your raspberry pi as a VPN node. You will need to have a laptop that is connected to the same network as your raspberry pi. This means that the wifi that you are connected on your laptop must be the same as the one on your raspberry pi. If you are new to using a raspberry pi, just YouTube how to flash your raspberry pi with a Raspberry Pi OS(32-bit) operating system. You will need a micro SD card for this and possibly a device that will connect your micro sd card to your computer. Once you are done with flashing the PI OS onto the SD card, you can then insert it into the raspberry pi device. Then power on and connect it to your wifi.
8. Ok so that was long to read but a must-understand for newbies.
9. So this step we will follow the instruction from the mysterious node setup page. You will need to SSH into your raspberry pi. Right here, you are basically remotely accessing your raspberry pi using the terminal or command lines from your computer. (Make sure you are on the same network as your pi).
10. Before you proceed with the next step, make sure you have the IP address of your raspberry pi. You can access this via your router page typically is 192.168.0.XXX and use the login info from your router box. Then look for your device list and find the IP address for your pi. Obviously Google and YouTube are also resources you can use.
11. So once you have your pi IP address, in the terminal of your computer, type: ssh pi@192.168.1.2 then ENTER(remember to use the pi address of your pi.)
- It will then ask you for your password which is usually, “raspberry” (As you type your password in, you will not see it. If you can’t proceed past this step, then verify you have the correct ip address and password.
- Here is the link in case you need help setting up ssh on your raspberry pi: https://itsfoss.com/ssh-into-raspberry
12. Once you’ve successfully access your pi via ssh, then you have completed step 2 of the myst node set up instructions. So now we proceed to step 3.
13. Type this into the terminal and press ENTER:
grep -qxF 'deb http://ppa.launchpad.net/mysteriumnetwork/node/ubuntu focal main' /etc/apt/sources.list || echo 'deb http://ppa.launchpad.net/mysteriumnetwork/node/ubuntu focal main' | sudo tee -a /etc/apt/sources.list > /dev/null
1. (Now you won’t get any return msg on this.) Next step type: sudo apt update 2. Now you may get an error here. It may say something to the line of the following signatures couldn’t be verified etc. So type this into the terminal if you are getting an error. 3. gpg –keyserver keyserver.ubuntu.com –recv-keys ECCB6A56B22C536D 4. I hope you just copy and paste above. It makes it a lot easier. 5. Once you press ENTER, you should get something like gpg: return on it. 6. Next type the following:
gpg -a --export ECCB6A56B22C536D | sudo apt-key add -
7. Once you press ENTER, you should get, “OK”.
8. Next type again, “sudo apt update” onto the terminal. You should be receiving msg such as Reading package lists…Done and with no error msg.
9. Then type, “sudo apt install myst -y”
10. Now it will go through its processing on the terminal. A blue background with Package Configuration will pop up. Click on TAB on the keyboard and press ENTER. And then a “YES” will be highlighted, press ENTER again.
11. Now it starts installing the package onto your raspberry pi device. And you should see a message that says installation successful.
12. Next step is to click on Claim Node. Then instead of waiting for the system to find your node, in some cases it won’t, just click on, “Claim Node Manually”.
13. This will take you to a new page which will show you the API address. Copy and paste the API address.
14. Go to your raspberry pi IP address. Per example above, we’ll just use 192.168.1.2:4449 (Be sure to type the IP address with the :4449 then press ENTER)
15. This will take you a new page to set up your node. Now as you walk through the set up of the node, you’ll need a METAMASK wallet address under the polygon network. You can google this if you are unfamiliar. Once you’ve set up your metamask wallet with the Polygon network, copy and paste your wallet address.
16. Paste the wallet address in there and click “Next”
17. Then select Buy MYST with Credit or Debit Card. It should be around $1 to obtain the MYST Tokens.
18. Click NEXT.
19. Once you’ve made the $1 payment the system will process the card. You will get an invoice that you can download once the payment is purchase is successful. Click NEXT.
20. Set up your very strong Password to access your Myst Nodes.
21. Then find the previous page where it has your API key. Copy and paste it onto the box below your password.
22. Once your registration is complete, a Myst Node Dashboard will pop up. Initially, you won’t see any traffic but with time users will pop up and you will start earning MYST tokens while providing VPN services to users from all over the world.
23. Quick reminder, if you are going from ethernet on your raspberry pi to wifi or vice versa, simply rebooting the pi will auto change the IP address. This will also work if your IP address of your router changes due to your dynamic set up.
24. Now that is it. You just set up your VPN node using a raspberry pi at the cost of $1 for myst tokens.
best
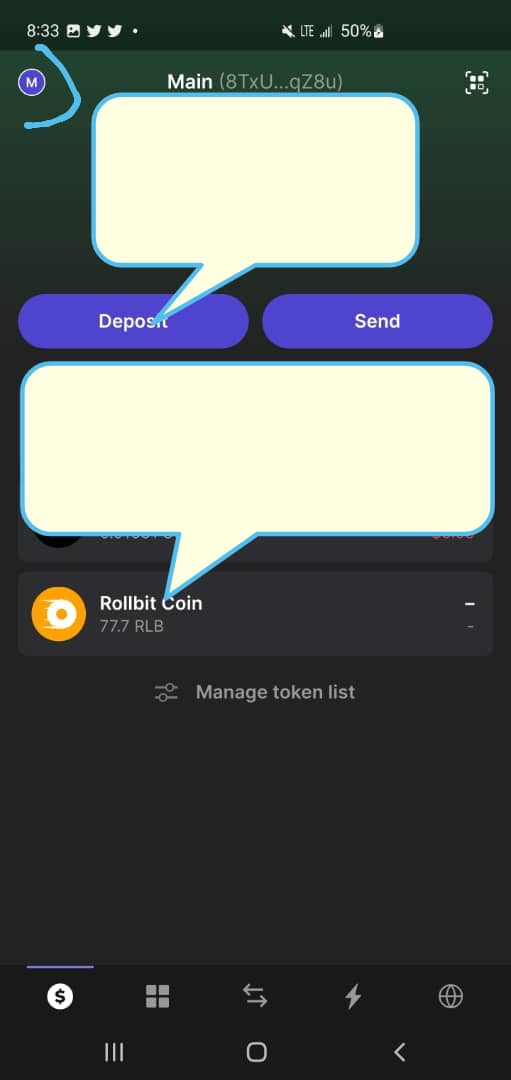
Platform: Phantom wallet(mobile)
Purpose: Fundz security purpose
Instructions:
How to revoke a connected site
This will help you disconnect for the site permanently after minting an NFT.
1. When you unlock your wallet, click on the top left corner 2. Go to trusted apps 3. Click revoke on every site.
Here are picture tips on how to do so.
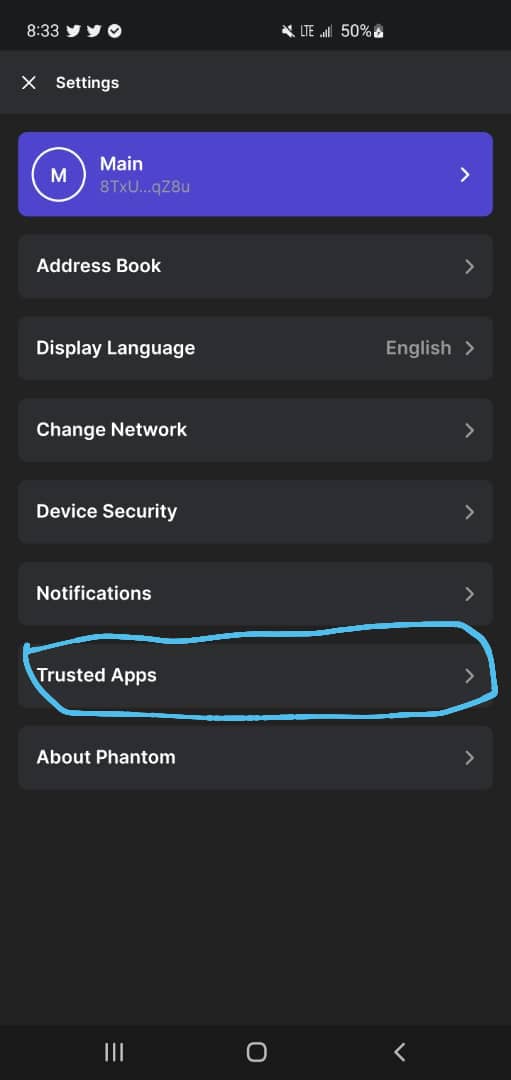
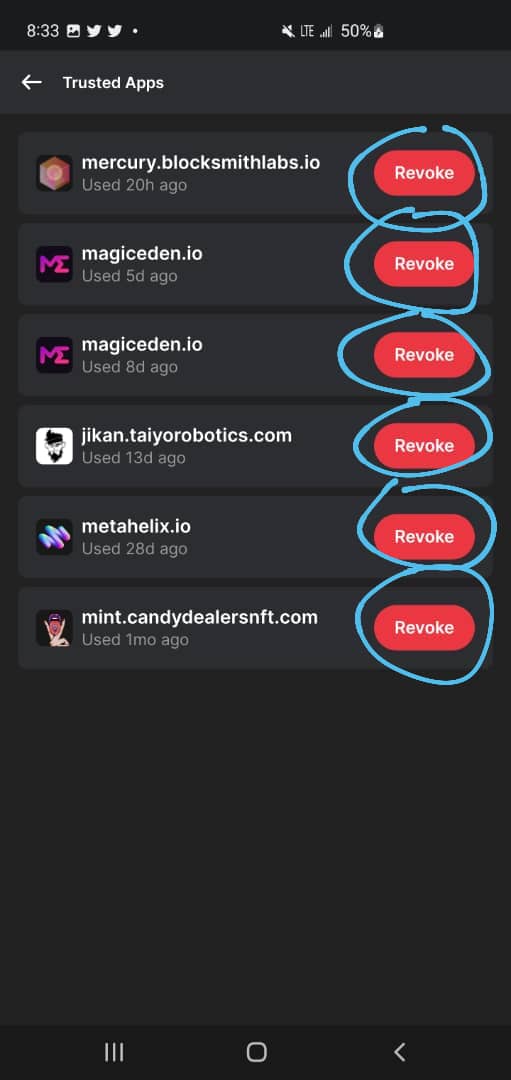
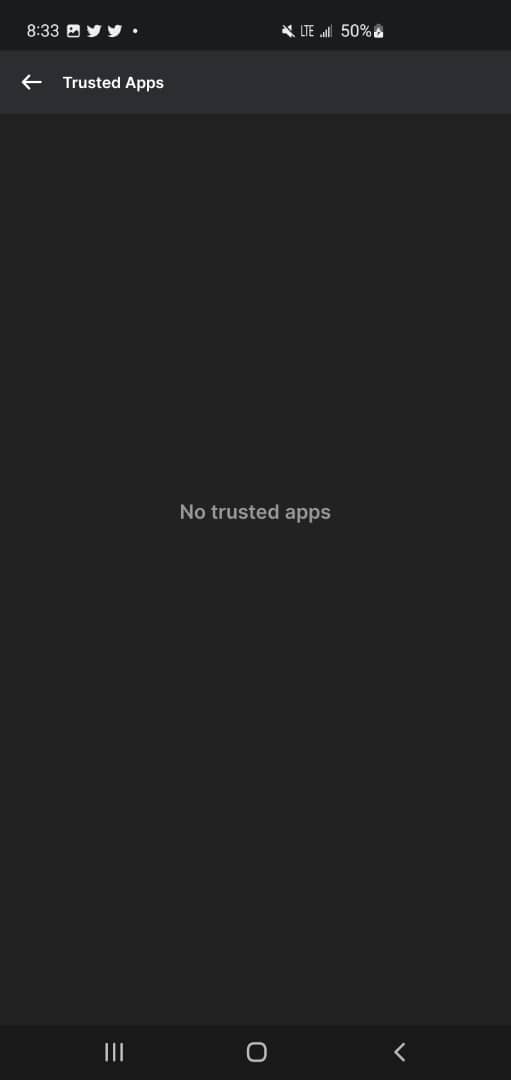
Olga Gorlova
Platform: CEX exchanges
Purpose: to ensure the security of your account on the CEX exchange
- Login Password
Used to sign in
- Verification
Used for verification when logging into an account, withdrawing funds, creating an API
- Phone
Used for verification when logging into an account, withdrawing funds, creating an API, etc. And can switch freely to Google verification mode (and vice versa).
- Email
Used to validate when outputting, creating an API
- Trading Password
Used for validation when translating, outputting, creating an API, etc. Please make sure your password is strong and save it.
- Restrict login IP address
Recommended for balance >0.1 BTC
If this setting is enabled, if you change your login IP address, the account protection mechanism will immediately activate and you will be automatically logged out.
To ensure the security of your account, please choose 「Google Verification + Link Email + Trading Password」or 「Link Phone Number + Trading Password」as the strategic security mode.
JULIA_Shu
Platform: Any VPN
Purpose: security rules when using a VPN
Instructions:
- To avoid account interception, it is important to use multi-factor authentication
- To reduce the vulnerability of the VPN client or gateway, update and patch regularly, use IP on the security gateway
- Do not enable VPN when accessing personal information, such as email, banking services or wallets
- Choose paid services VPN and those that have been operating on the market for many years
Join our newsletter to stay up to date on features and releases